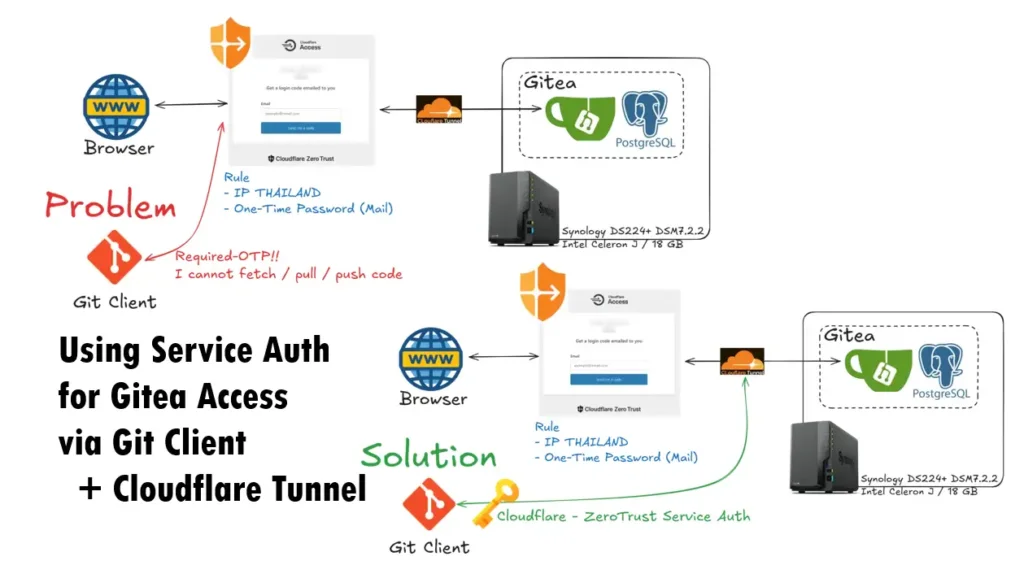
previous, I added a Cloudflare Zero Trust Application Access for my gitea with a one-time password, but when I use a git client to push code, it redirects me to Cloudflare Tunnel with a one-time password
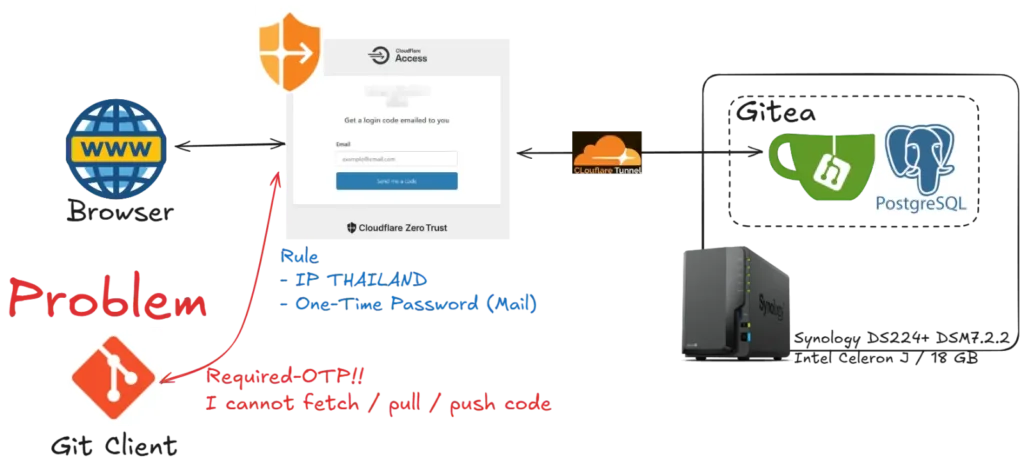
So, in this blog, I want to create a Service Auth to ByPass access to Gitea, if I have a special key. Otherwise, it redirects to Cloudflare Tunnel with a one-time password

Table of Contents
Set up Gitea + Cloudflare Zero Trust Application Access
If you have already setup Gitea + Cloudflare Zero Trust Application Access. You can go to step setup Create Service Auth (For Git Client to Access)
🛡️ Set up Gitea
For Gitea, which I chose to use because GitLab was consuming more and more resources, and in newer versions, some features were moved to paid tiers. Compared to the First GitLab version I was using, which was probably version 13, For investigated a problem with the Root user breaking the branch protection rule issues, so I used it for a long time until I changed machines, the last is 17.4.
Now 2025, I moved my homelab to Synology NAS, so I chose Gitea because it's lightweight and has the Merge Approval feature that disappeared from GitLab.
I have a Docker Compose file ready for deployment (I use it on my Synology NAS)
For documentation about Gitea installation details, please go to Gitea - Installation
🛡️ Check Authentication on Cloudflare Zero Trust
Check Authentication on Cloudflare Zero Trust Trust Overview > Settings> Authentication
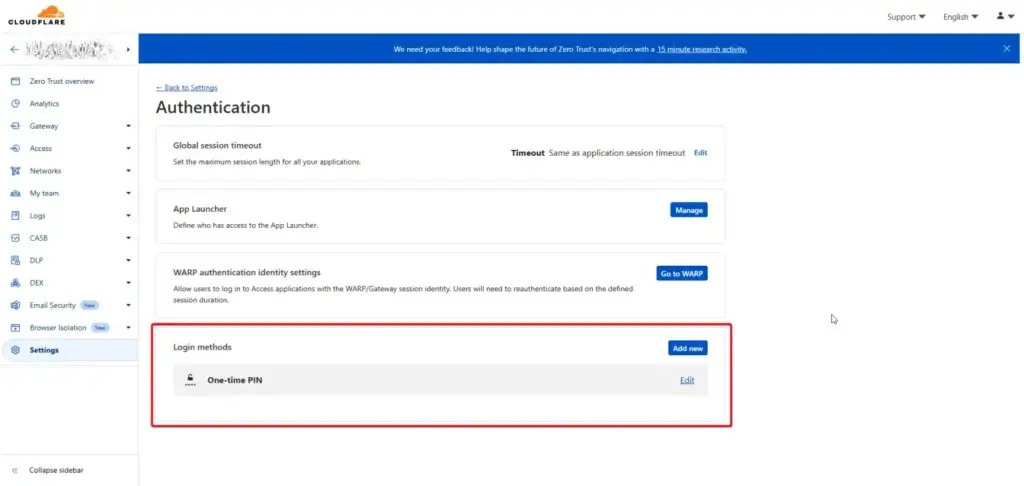
The default is Email One-Time Password, but you can set another method, such as Azure AD (Entra Id) / Open Id, etc.
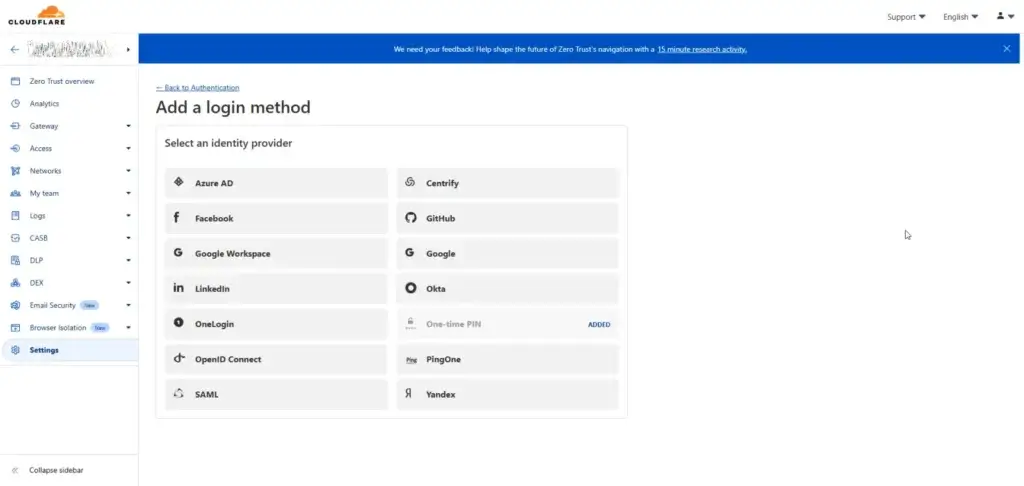
🛡️ Add Application Policy
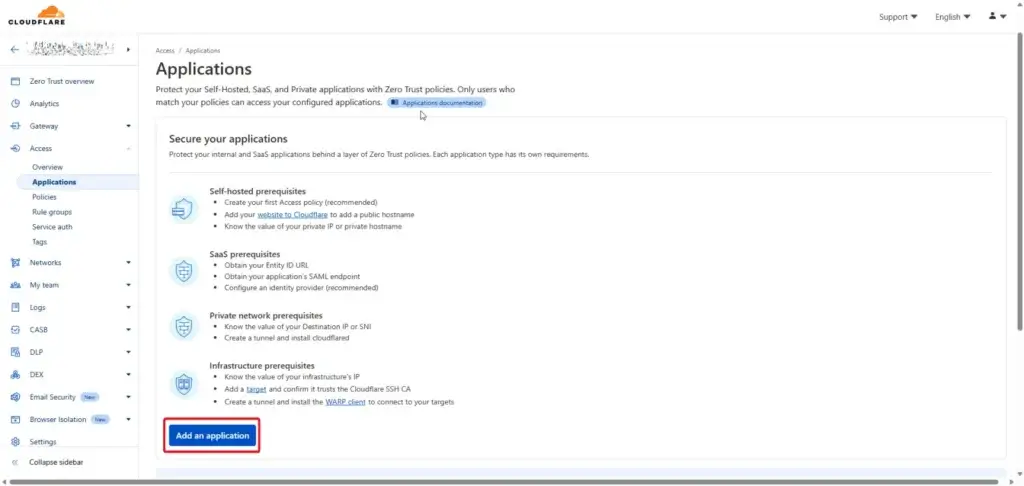
Zero Trust Overview > Access > Application
- Add Application
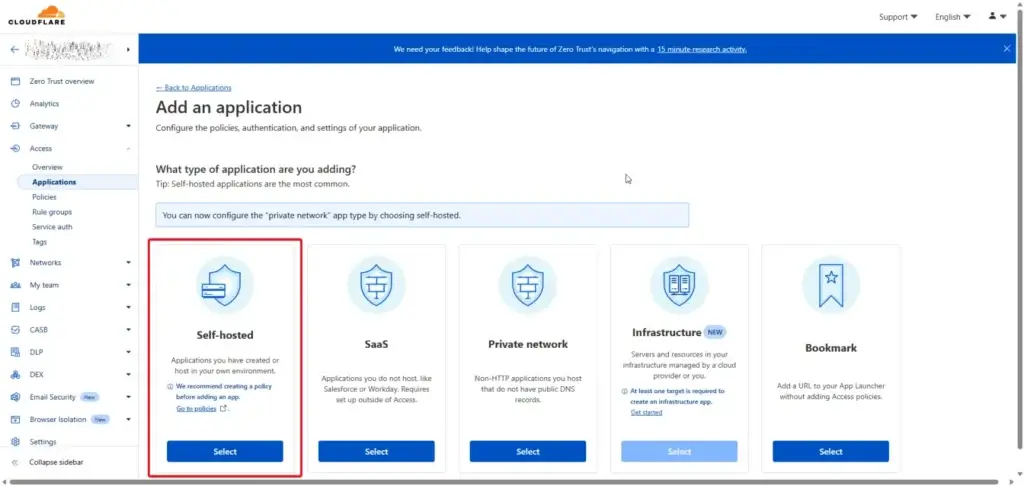
- Select Self-Hosted (In this case in run App Gitea on Synology)
- Create you General Info
- Config Name
- Domain + Sub Domain + Path to Access

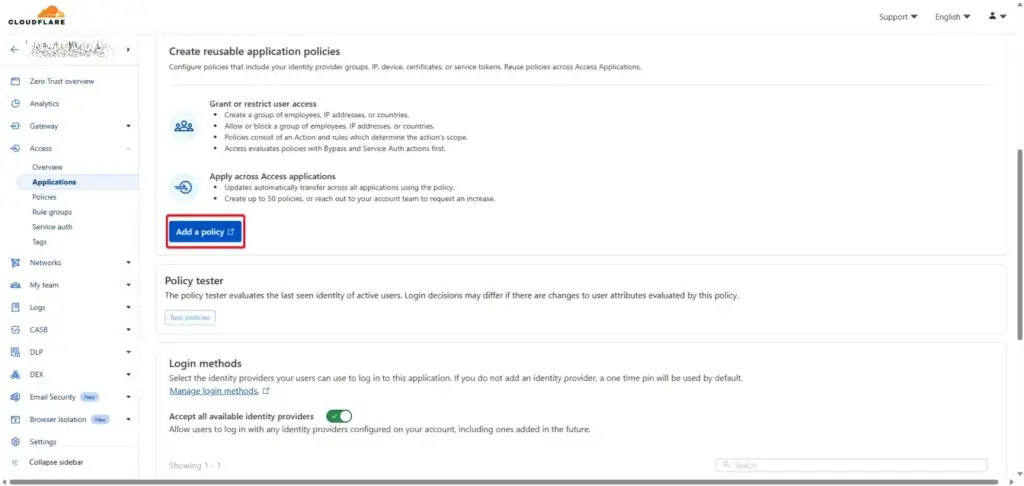
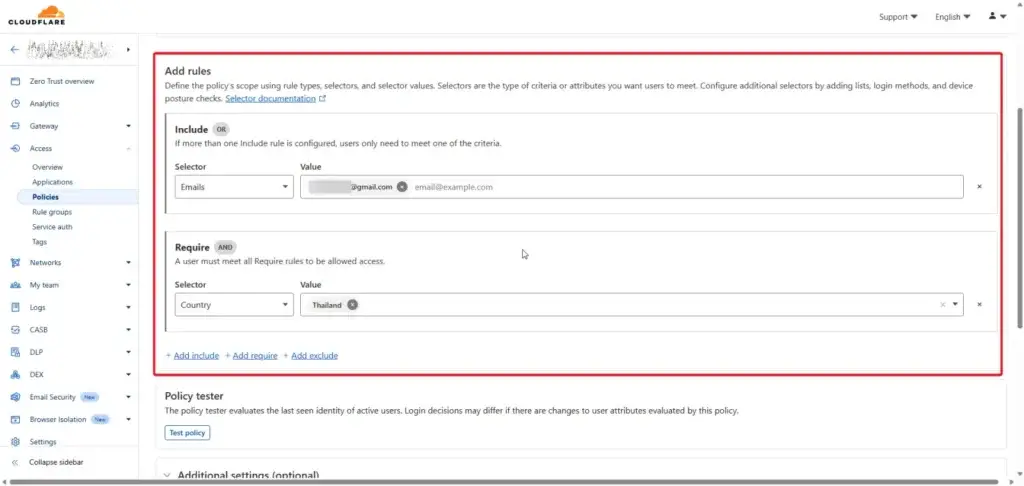
Next Add a Policy you can
- create a new policy (Add Policy)
- or use existing
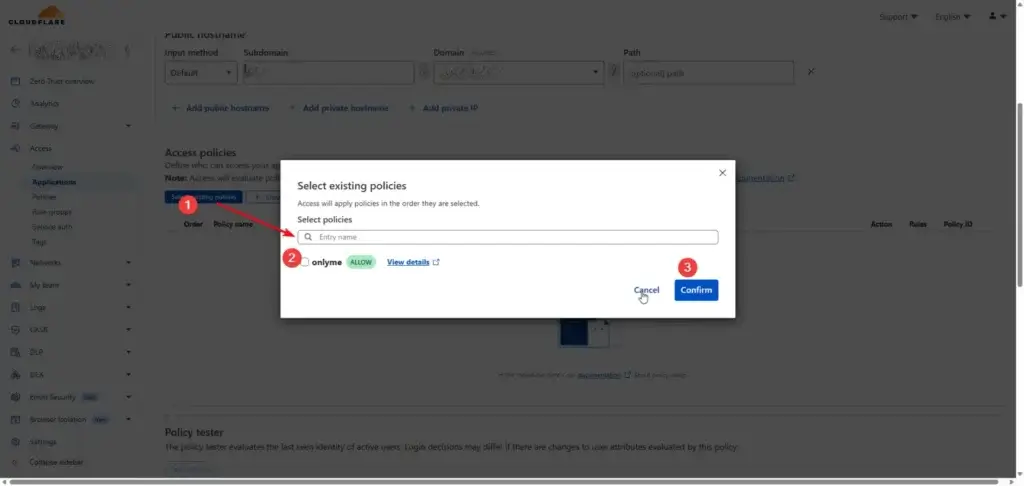
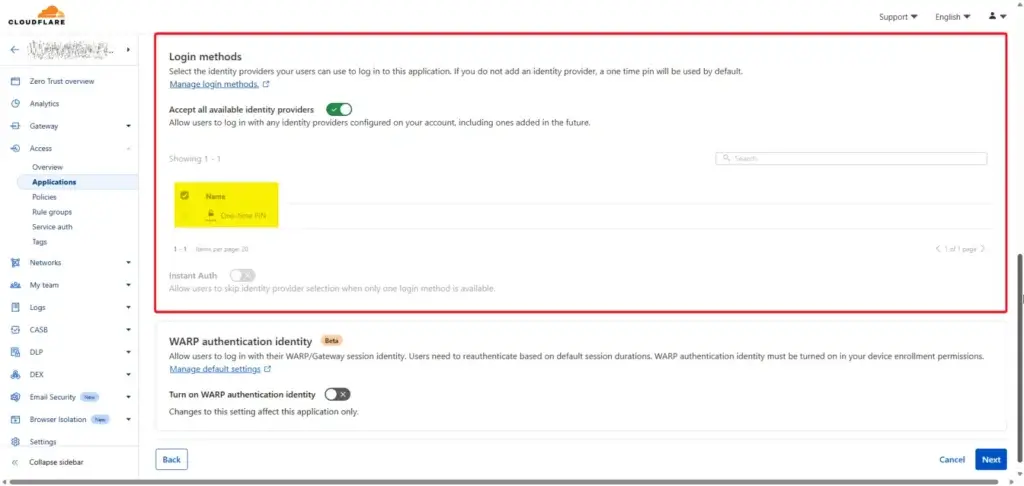
Next, Select the Authentication Method (I use Email One-Time Password)
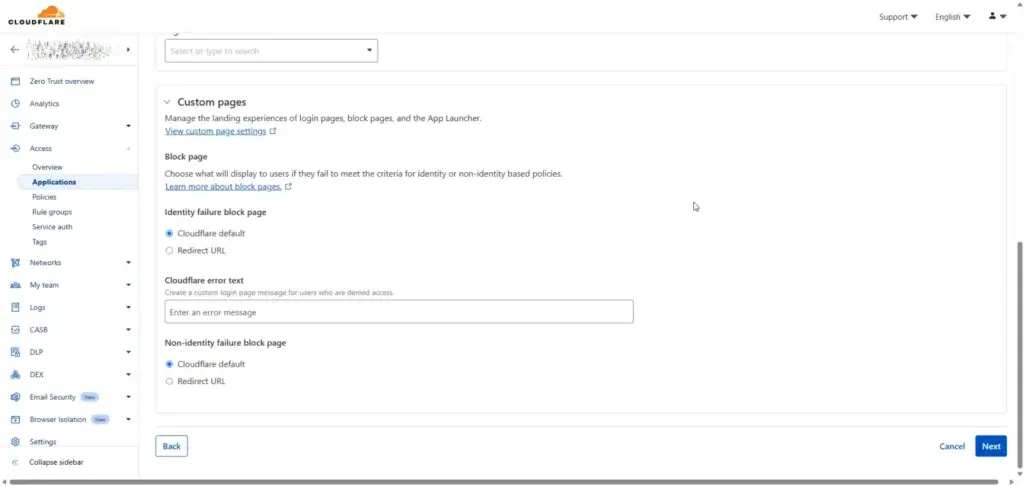
You can customize such as custom login page
📌 Test via Web Access, such as https://yourgitdomain
- From the Gitea Login Page, redirected to the Cloudflare Access Page
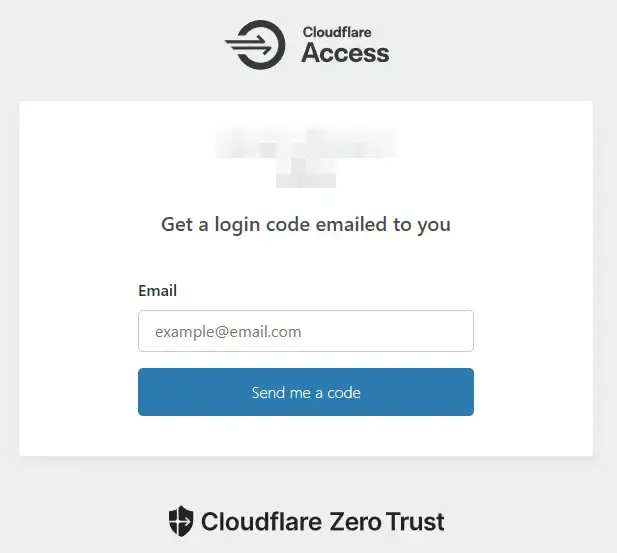
- Cloudflare will send a one-time password

- Enter one-time password, if the correct code is entered, you will be redirected to the Gitea Login Page. Enter your Gitea Username + Password. You will see a dashboard
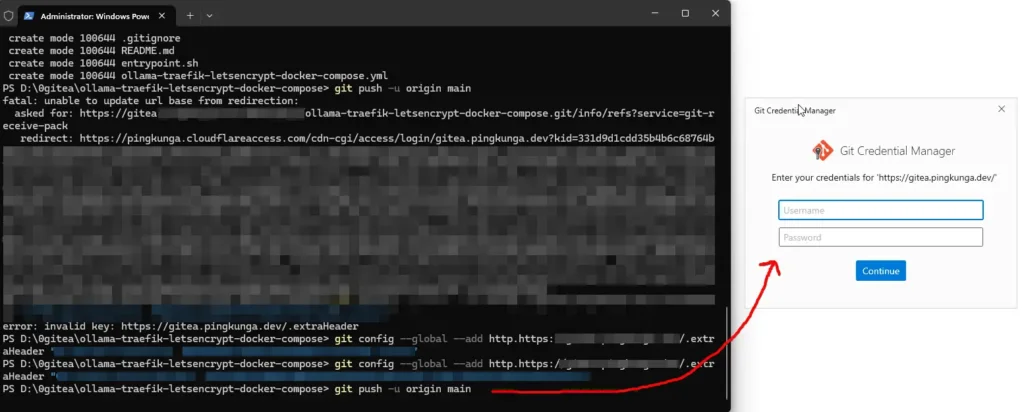
But when using Git Client to push code. I required a One-Time Password like this
PS D:\0gitea\ollama-traefik-letsencrypt-docker-compose> git push fatal: unable to update url base from redirection: asked for: https://gitea.youdomain.example/samplegitusr/ollama-traefik-letsencrypt-docker-compose.git/info/refs?service=git-receive-pack redirect: https://xxxxxxxx.cloudflareaccess.com/cdn-cgi/access/login/gitea.youdomain.example?kid=33FQu...&redirect_url=%2Fsamplegitusr%2Follama-traefik-letsencrypt-docker-compose.git%2Finfo%2Frefs%3Fservice%3Dgit-receive-pack
Create Service Auth (For Git Client to Access)
So, in this blog, I want to create a Service Auth to ByPass access to Gitea, if I have a special key. Otherwise, it redirects to Cloudflare Tunnel with a one-time password

🛡️ Create Service Auth
- Cloudflare Zero Trust Dashboard > Access > Service Auth > Create Service
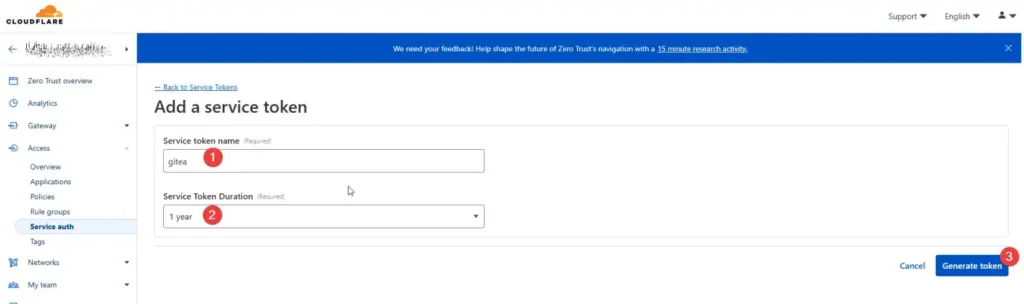
- Save CF-Access-Client-Id / CF-Access-Client-Secret, for adding in the git client

🛡️ Create a ByPass Policy

- Cloudflare Zero Trust Dashboard > Access > Policies > Add Policies
- Create a ByPass for Gitea with condition Service Auth (gitea)
🛡️ Add Cloudflare Zero Trust Application Access
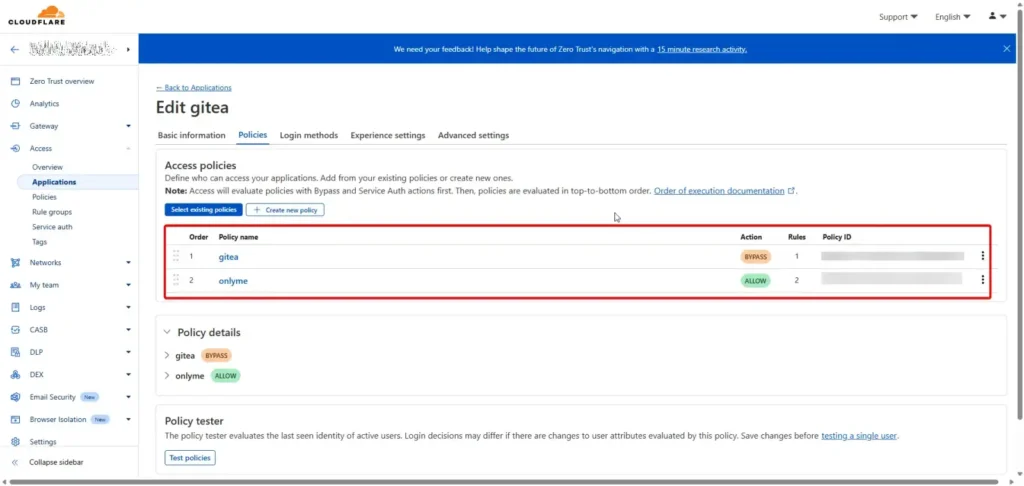
- Cloudflare Zero Trust Dashboard > Access > Applications > Add an application > Self-hosted
- Set Gitea Domain
- Add Policy First
1. ByPass Policy (Service Auth)
2. One-Time Password, if the ByPass Policy does Not Match
🛡️Configure your git config with the Service Auth header
Run the following command to tell git client to add an extra header with the Gitea URL
git config --global --add http.https://yourgitdomain/.extraHeader "CF-Access-Client-Id: CF_Service_Auth_Access" git config --global --add http.https://yourgitdomain/.extraHeader "CF-Access-Client-Secret: CF_Service_Auth_Access_Secret"
📌 Test
Reference
Discover more from naiwaen@DebuggingSoft
Subscribe to get the latest posts sent to your email.